Cybersecurity scan feature
Horangi’s cybersecurity scan feature enables users to conduct and schedule scans to detect vulnerabilities in their applications, networks, repositories, cloud, and endpoint devices.
Dashboards displaying information and statistical graphics inform users of their security posture, and usability is enhanced with storytelling, and gamification.
Scan page design
The scan page allows users to group endpoints and schedule scans.
Target users are primarily non-cybersecurity proficient, relying on clear actionable cues to solve security issues and remediate vulnerabilities.
Target users are primarily non-cybersecurity proficient, relying on clear actionable cues to solve security issues and remediate vulnerabilities.
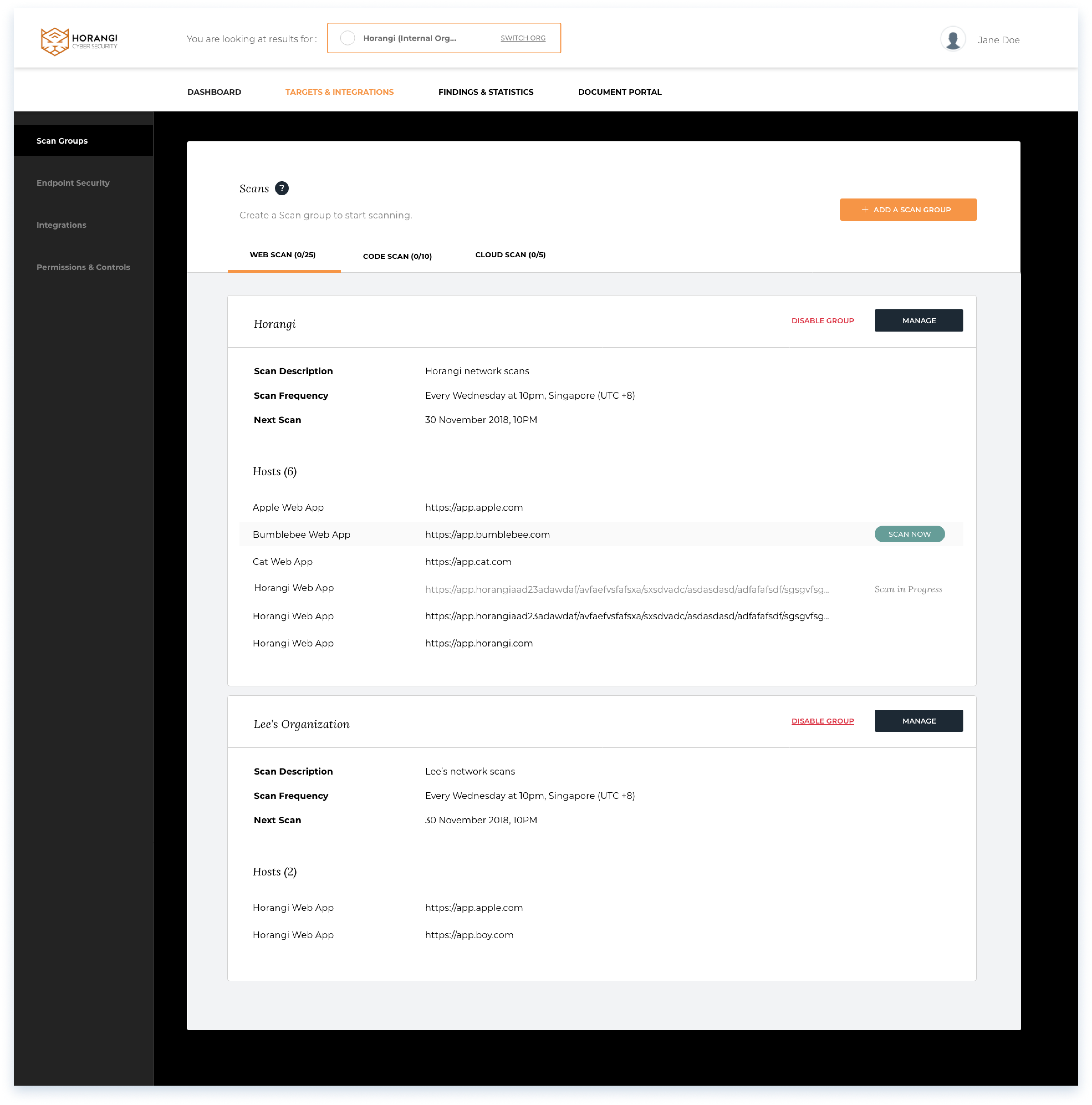
Creating a scan group
A scan groups allow users to conduct and schedule scans.
Users can create Scan Groups, to allow the grouping of scan targets by scan frequency.
Users can create Scan Groups, to allow the grouping of scan targets by scan frequency.
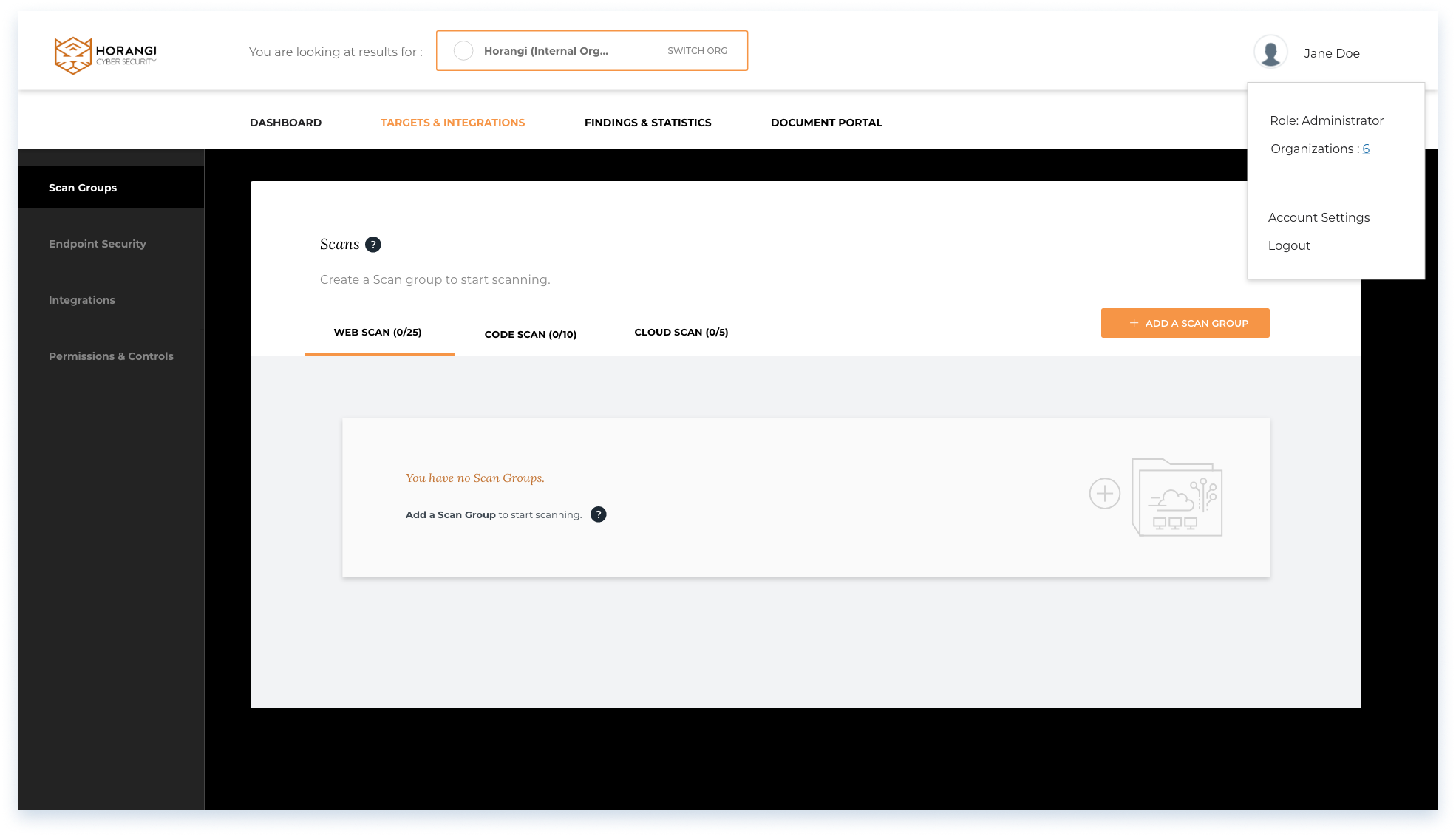
Empty scan page
Users start by creating a scan group under the Targets & Integrations tab. The small card within the grey area of the interface contains simple instructions to guide users.
By clicking the tooltip, users can access additional information and choose to prompt a walk-through tutorial.
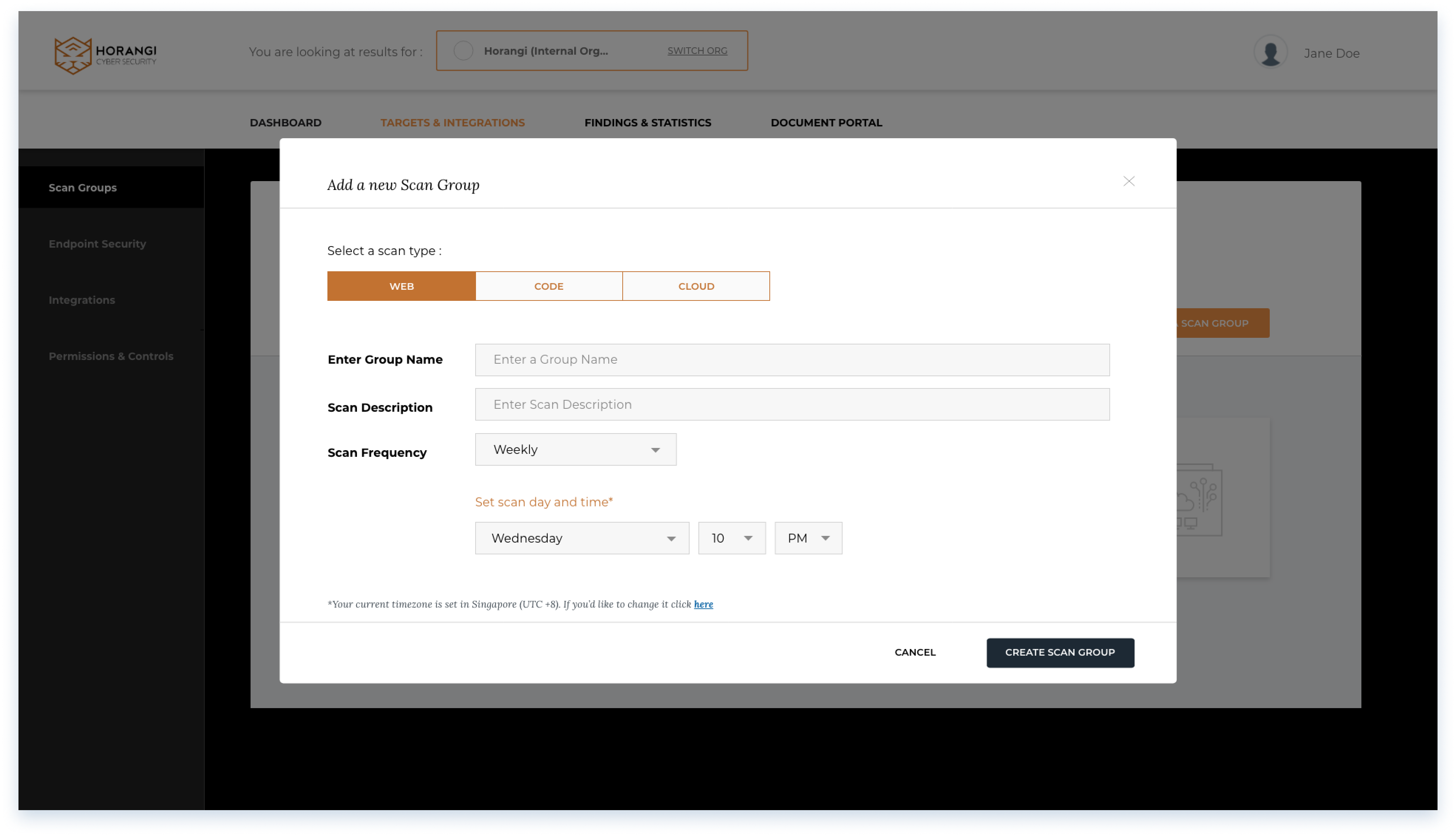
Add a scan group
Users configure the scan group by defining the scan frequency and schedule timing.
A timezone reminder is included, with an link to redirect to settings if needed.
Scan group created
A successfully created scan group will appear as a card depicting all necessary details.
Users can click on the ‘Manage’ button to add targets within their configured scan group.

Manage scan groups
On the page for managing scan groups, users can:
- Edit Group details and reconfigure scan frequency
- Verify, scan, and disable scan targets
- View Scan status and last scanned
- Conduct impromptu scans
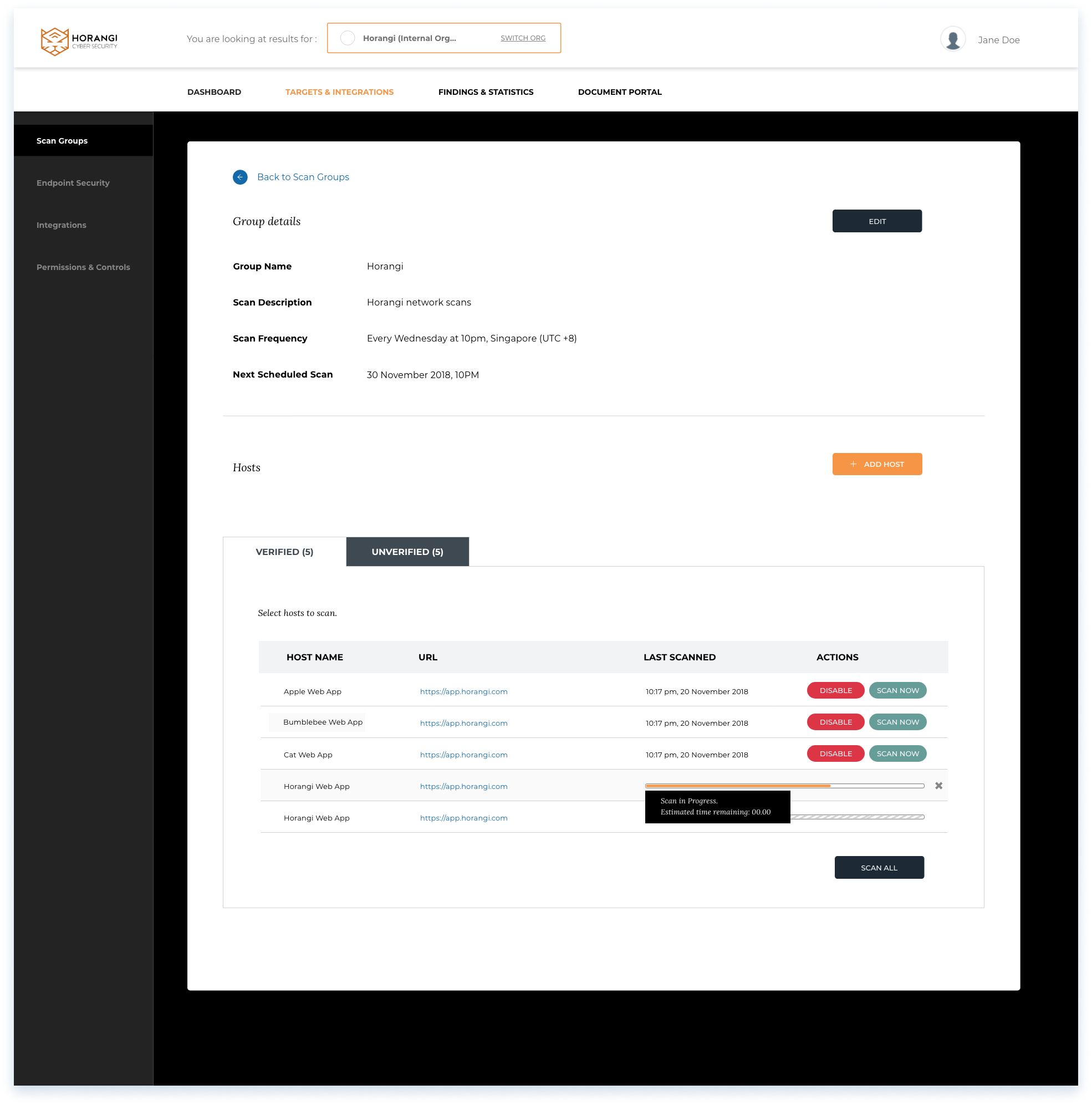
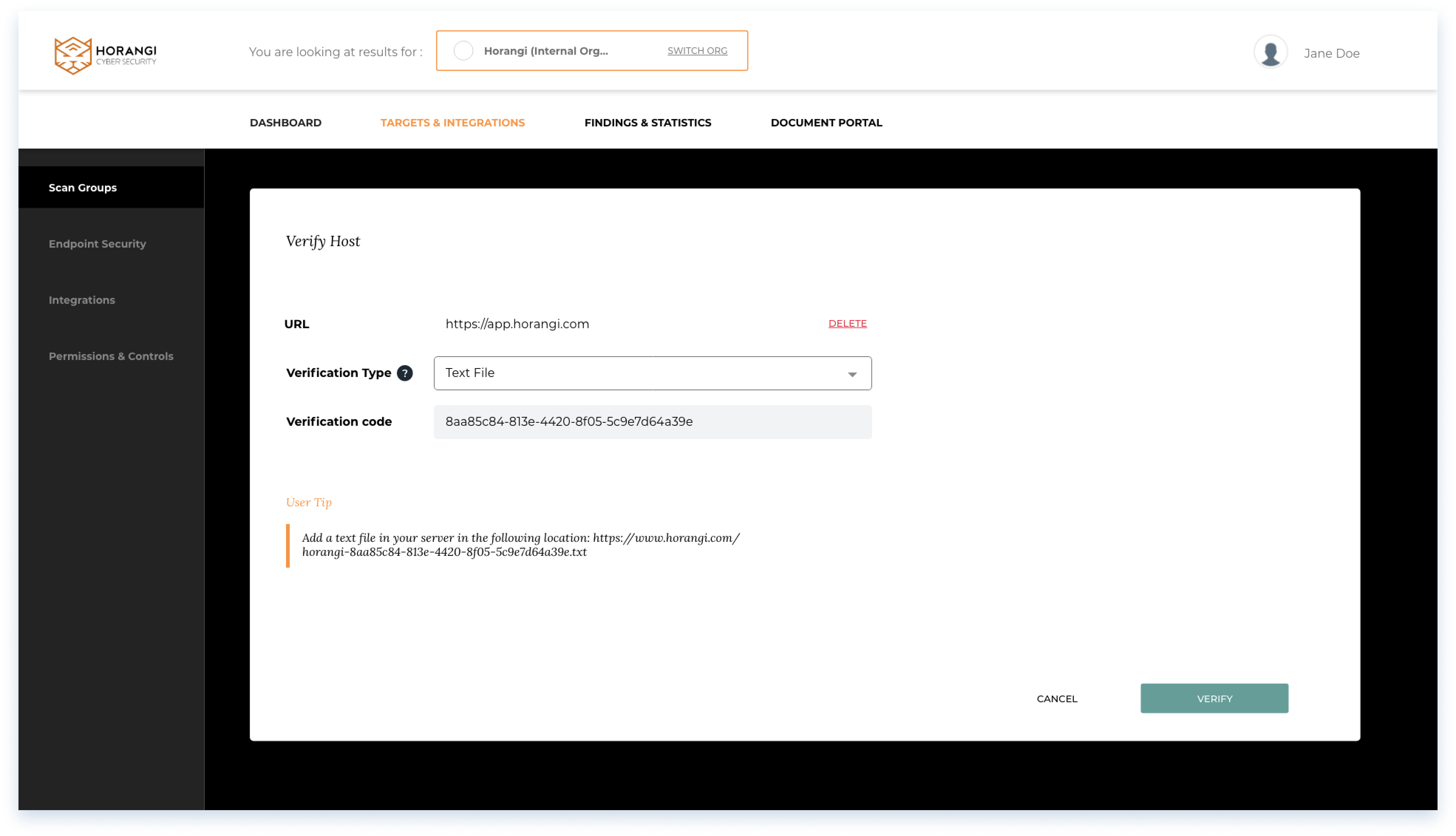
Additonal steps: Host verification
The below screen shows a standard format for additional steps, in this case host verification for networks.
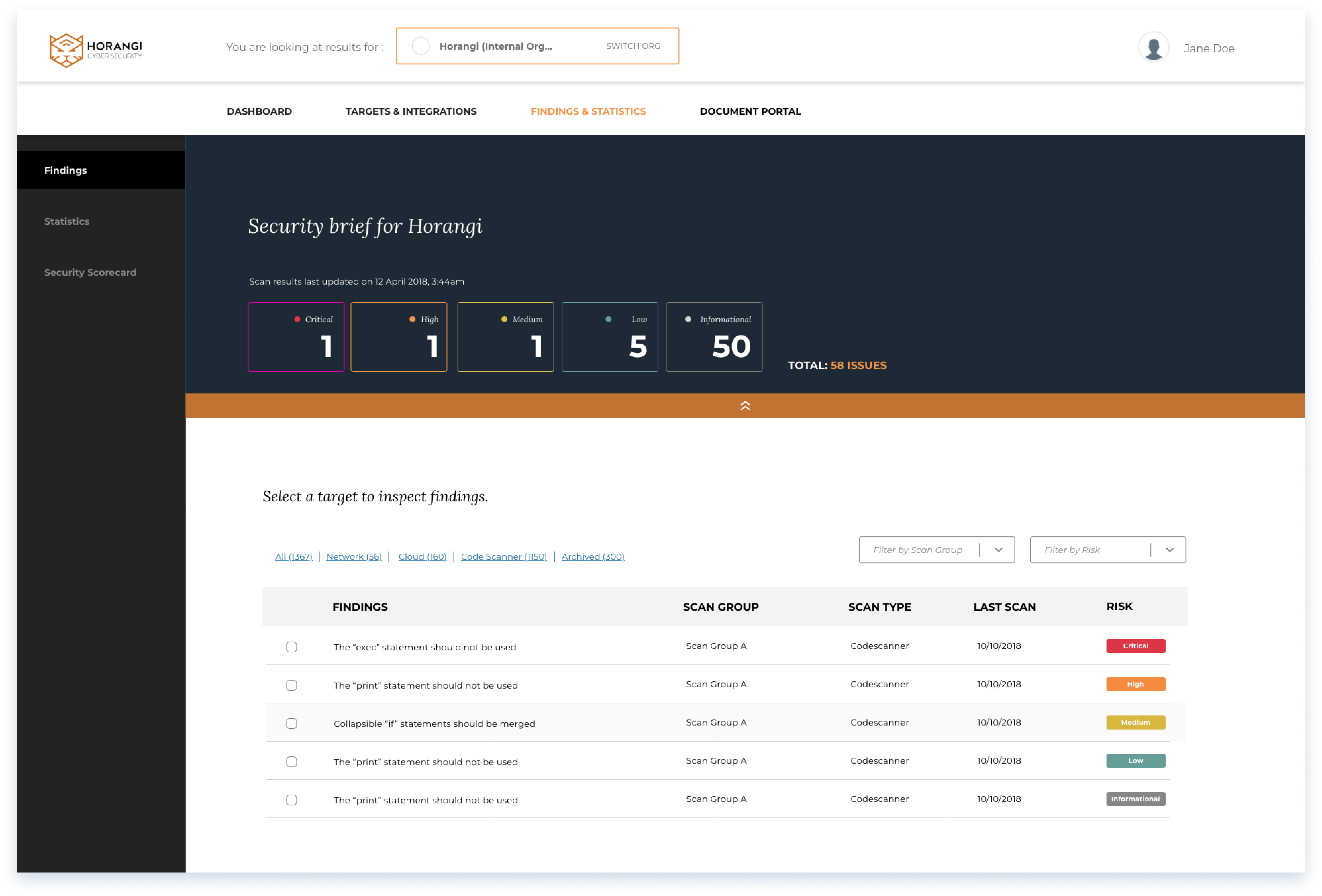
Security brief
The findings page displays vulnerabilities detected from each scan.
Findings dashboard
A collapsible dashboard shows staple statistics. Sort and filter functions are present for users' convenience.
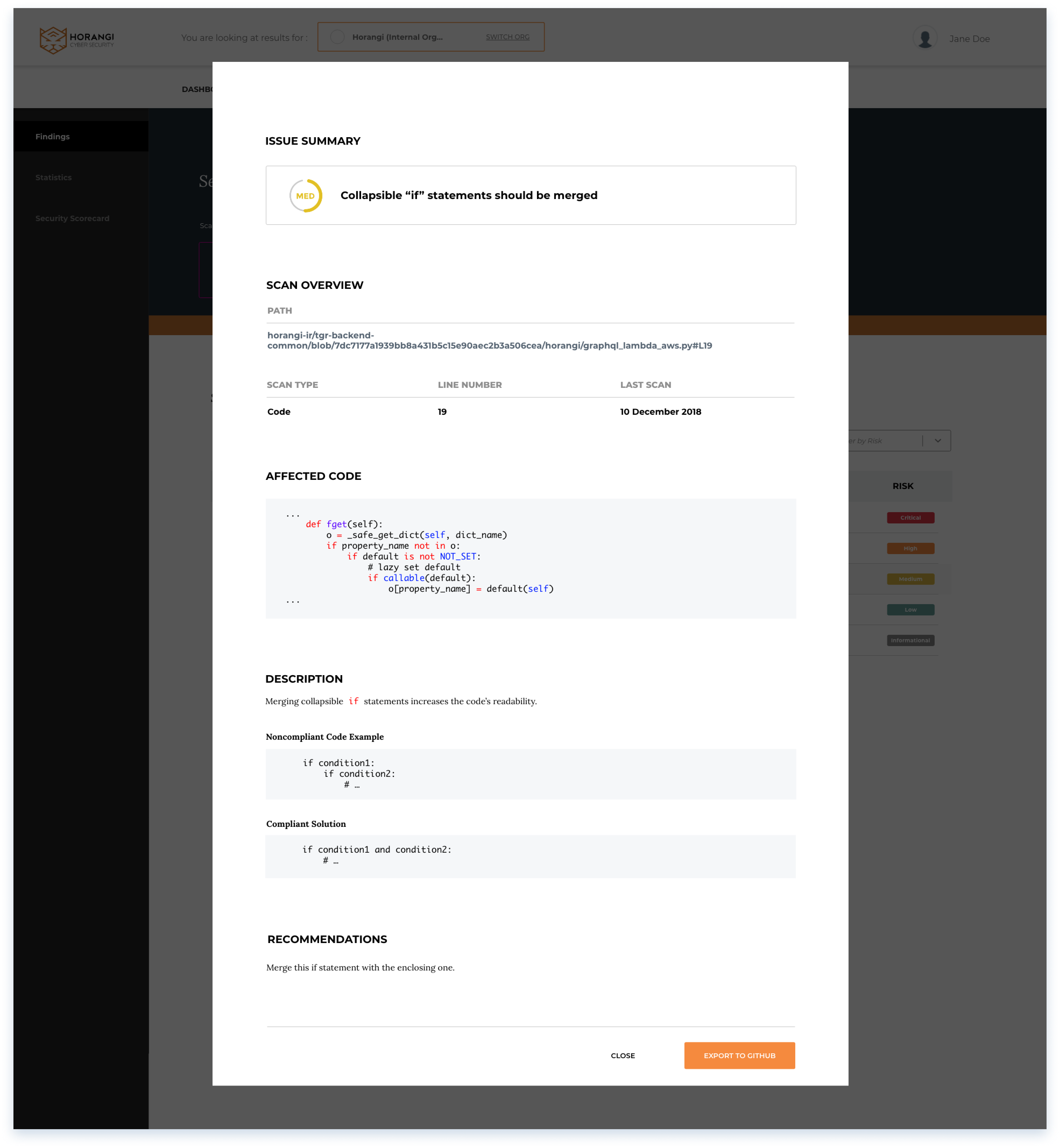
Issue summary
When a user selects a finding, a breakdown summary of the inspection is presented in a pop-up format.
Users can also export the finding to a project management tool of their choice.
Gamification the of Security Posture Scorecard
The security scorecard allows users to engage in the understanding of their security posture, and review various factors that affect their scores.
Security Scorecard page

Score breakdown
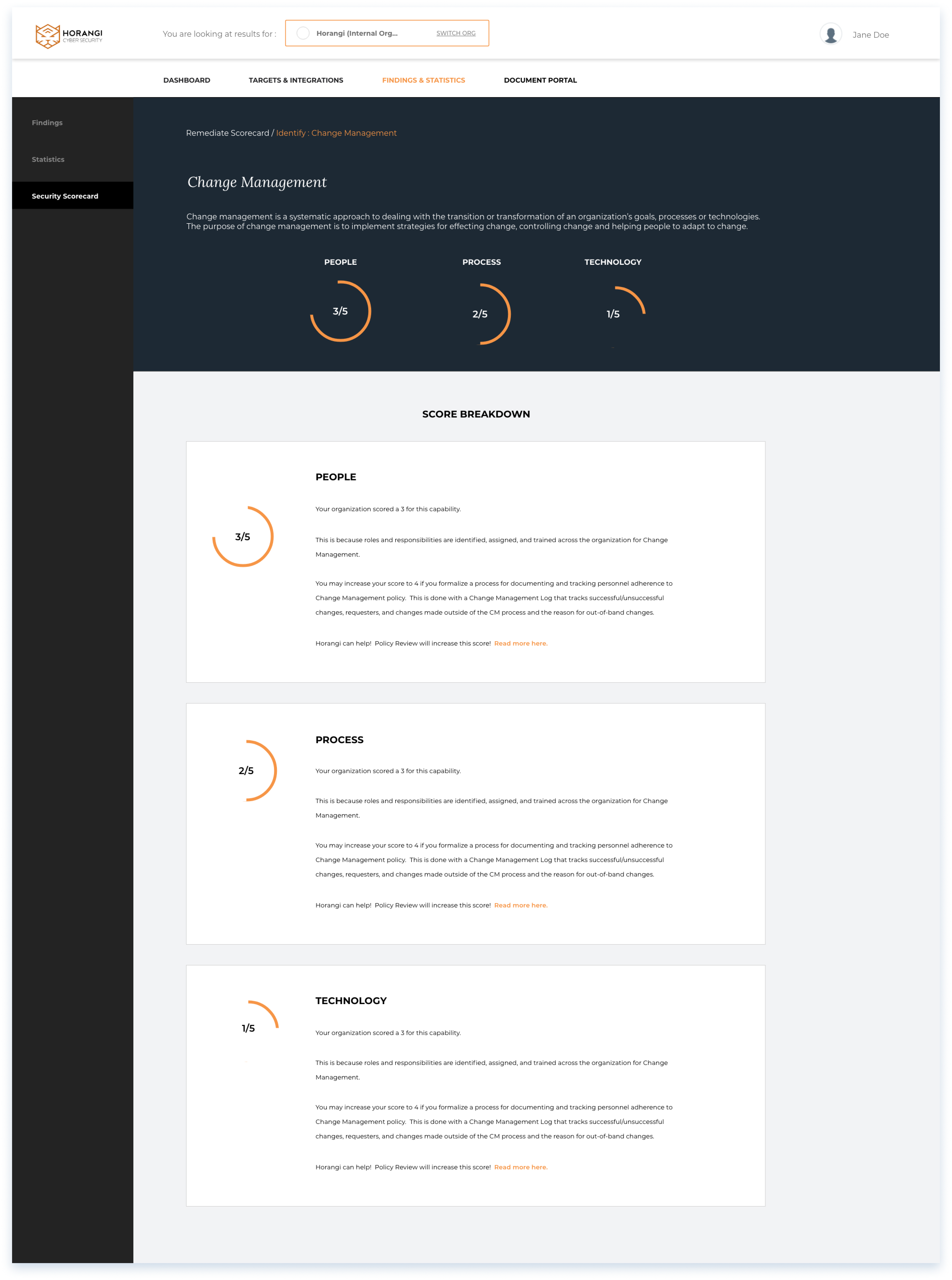
Illustration work
Custom illustration created for the security posture placeholder.
